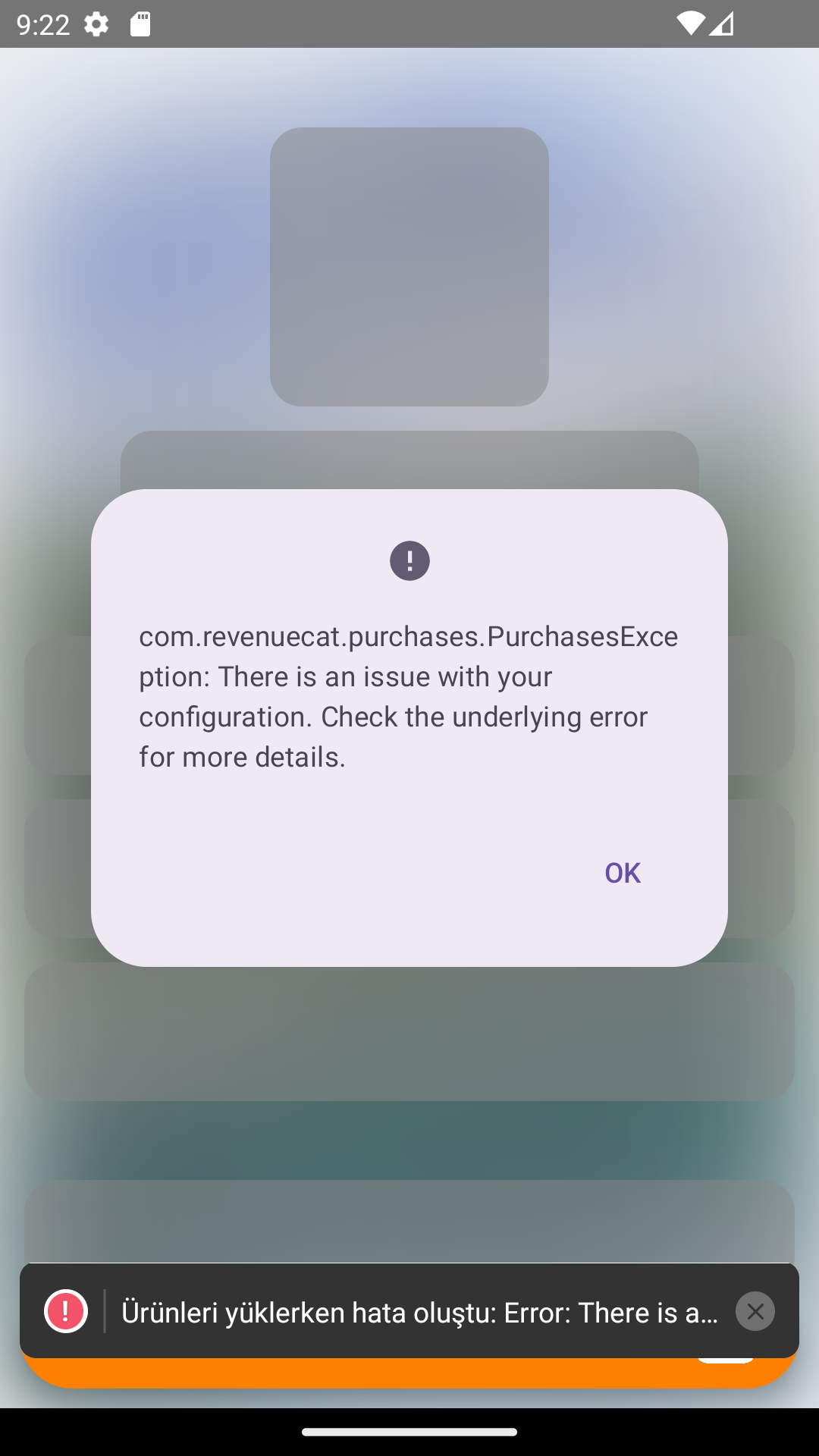
Hi I am seeing this message in my App Store Connect,
-
The SHA-1 intermediate certificate used for signing App Store receipts expires on January 24, 2025. If your app performs on-device receipt validation, make sure it supports the SHA-256 algorithm; alternatively, use the AppTransaction and Transaction APIs to verify App Store transactions. Learn More
I checked the docs but couldn't find anything regarding that.
Is there something we should do?
I am using Flutter in my client with version: 8.2.2.